Many have heard of phishing , vishing , and smishing , terms which have flourished to describe the ways in which people are tricked into sharing their personal information. These attack techniques are often associated with online fraud, but they in fact belong under a much wider umbrella we call ‘social engineering’.
Social engineering is a broad term for many different activities, but they all boil down to a common denominator: using human interaction to nudge people into helping the perpetrator achieve a goal, often a malicious one. Different types of social engineering attacks are often combined depending on the antagonist's wants. Social engineering is only a set of tools to reach the end goal. For example, compromised log-in details may be used to gain access to a computer system so the attacker can steal data or plant malicious code. Alternatively, an attacker might hack into all your online bank accounts; take out loans in your name; or steal your identity to be used to set up a company. The list could almost be indefinite. It is, however, essential to note that even if many social engineering attacks are cyber-enabled but they can also be carried out physically, or face-to-face. It can be hard to detect the use of social engineering since it relies on exploiting our human nature and vulnerability. In other words, we often want to help, trust, and believe what we see, and a person can abuse all these attributes with malicious intent. So, let's dive into this topic and illustrate what these techniques are and what sets them apart from one another.
Reconnaissance
Social engineering attacks often commence with a reconnaissance phase, where an attacker maps out information about a victim. This could be mapping out a company network and computer system, or canvassing employee structures, emails, phone numbers and more. It can also be in the form of surveillance of a company perimeter, photographing entry and exit points and key staff. Note that these are just examples, and only your imagination sets the limit.

Phishing
The most common social engineering attack goes under the term phishing . Phishing is derived from ‘fishing’, where I, as an attacker, go on a fishing expedition and, if I'm lucky, I might get a bite and reel in a big catch.
We commonly see this in the form of unsolicited emails. The sophistication of such emails can vary, from the well-crafted to the poorly constructed, and everything in-between. To do this, an attacker often uses premade tools which can efficiently distribute emails en masse – for example, the Social Engineering Toolkit. There are plenty more openly available tools to streamline social engineering attacks.
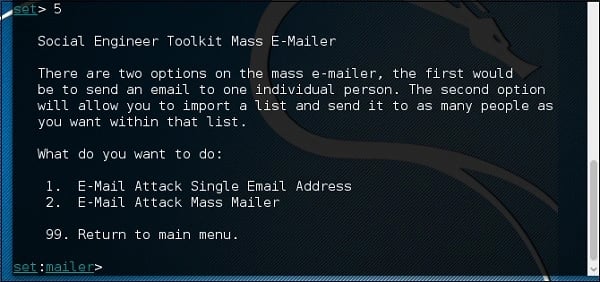
So, what is the point of doing this? It depends on the attacker's ultimate intent; but, invariably, the object of a phishing attack is to make a recipient open the email and trust the content and sender. Suppose the purpose is to steal your credentials: in that case, the email may contain a link to a website that closely resembles one you already trust, which may ask you to input sensitive information. The website could also download malicious code and infect your computer system – or the email itself might contain malicious code.
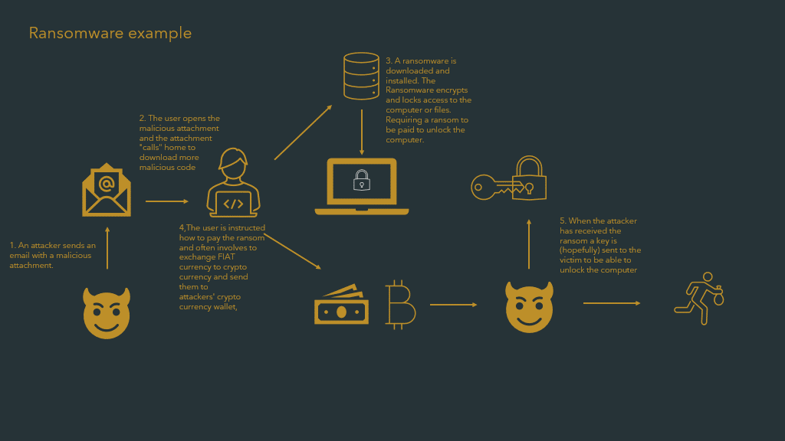
A phishing attack which aims to infect the victim’s computer with a ransomware virus might look like this:
Some variants of phishing include:
Spear Phishing: when a specific person or organisation is directly targeted.
Whaling: when a person of high wealth or influence is targeted.
Vishing: a combination of ‘voice’ and ‘phishing’, describes scenarios where an attacker contacts potential victims via telephone call and tries to extract information or gain access to their computer systems or, for example, bank accounts.
Smishing: where an attacker uses SMS-based messages to trick potential victims into clicking links that lead to a malicious website – which can often look like a legitimate website – and prompts the victim to fill in sensitive information.
There are several more methods under the Social Engineering umbrella. All of these methods can be combined in an attack chain. For example, they can be used in phishing, but they can also be acted out on their own or in a combination of other methods.
Pretexting
Pretexting is a social engineering tactic whereby the attacker creates a staged scenario (or pretext), interacting with the victim in order to ‘set the scene’ for the attack. The whole point of pretexting is to make a victim believe the background story presented in order to gain their trust. Pretexting can be cyber-enabled or physical in nature. For example, it is often used in phishing attacks, where the perpetrator tries to represent that they are someone they are not, and lures or persuades the victim to perform specific actions. The victim is often motivated by the prospect of a reward, or responding to perceived duress. This can also be executed by walking into an office while pretending to be maintenance staff or someone in a position of authority. The perpetrator may, for example, also send an email to the front desk before the intrusion attempt, purporting to be management informing reception staff of an upcoming visitor. It is surprising how far onto a premises one can get with an ordinary reflective vest and a hard hat; acting in an authority role; or even just delivering pizzas at lunchtime.

Totally trustworthy person who does not need an access badge
Tailgating
Tailgating is when one tries to sneak into a restricted-access building or premises, by following staff (or others with access) through the gates. This can also be combined with pretexting, where, for example, one pretends to be someone who should have access (such as the benevolent pizza delivery guy) and kindly holds the door open for staff, only to sneak in behind them as they pass.

Baiting
When an antagonist has successfully entered a premises, or used reconnaissance to find out where approachable targets gather, they may use additional tools to gain further access to information. One such method is called baiting. Here, the antagonist might, for example, leave behind a USB stick in the hopes that it will be found by a curious employee who will insert it into their computer – which may be especially tempting if the USB stick is cleverly labelled “my super-secret files”. Once the USB stick is inserted, malicious code will run to exploit the company network.

Quid Pro Quo
Ever heard of “I scratch your back, you scratch mine”? This method is an exchange of services, where an attacker has something to offer a potential victim that might aid in a grander attack scheme. For example, “I will reward you if you give me the admin password to your email servers.”
Honey trapping
Honey traps have been used throughout history, luring a victim in with a false hope of finding love. This is very common nowadays in what is called romance scams, executed to defraud a victim. However, state actors also use this method to gain access to information or sources of information. Romance scams are growing rapidly and take intriguing forms, with fraudsters pretending to be everything from soldiers in the need of aid to an astronaut returning to earth . Many will laugh at these scams and think that the victim is very gullible – but one must also remember that the quest for love is one of the most potent drivers embedded deep into our human psyche.

Scareware
Scareware is similar to ransomware. However, where ransomware locks users out of computer systems, encrypts and possibly destroys files, scareware is more of a nuisance, made to scare and distress a user into paying to get rid of harmful software. Often this manifest as a pop-up (or several pop-ups) on a computer or browser stating that the computer is infected with a virus, and providing a support number for help. Over the past years, this has materialised in frauds known as "tech support scams". When the victim calls the support number, the fraudster will further cement the story that the computer is infected, requiring that a sum of money be paid to get rid of the virus. Usually, the payment will be made by gift card, as the fraudster will advise the victim that their regular credit cards are not working. Fraudsters prefer payment by gift cards as they are more anonymous, often paid with cash and therefore less traceable.

Waterholing
Waterholing is a clever attack method. In simplified terms, it is an attack against a website or a part of a supply chain service (software application or device) that intended victims often visit and trust. It can also be a ‘lookalike' website, where the domain name and appearance are a copy of the standard website a victim visits. In the example of the website, or its lookalike, it gets infected with malicious code which then spreads to visitors, whose own computers and connected systems will then be compromised.
For example, in 2017, the Polish Financial Supervisory Authority detected a waterholing attack on its website which had commenced in 2016. Banks are frequent visitors on websites belonging to Financial Supervisory Authorities and were the intended victims of the attack. Not all visitors could be infected; only visitors from specific IP addresses belonging to a mix of public and private financial institutions were targeted.

BEC
Business Email Compromise is a crime that often combines several social engineering techniques. The goal is to compromise a user and corresponding business email. Once compromised, it can go different routes. It can develop into what is known as CEO fraud, where the email that has been compromised belongs to a C-level persona, and that email will be used to convince a finance employee to send money to a fraudulent receiver. Alternatively, it can often develop into a compromise of business systems. For example, customer relationship management systems, and/or invoicing and order systems, can be targeted to change invoicing and shipping details. This can lead to massive losses due to funds being rerouted to fraudulent bank accounts, or shipments being made to fraudulent addresses.
Deep fakes
Deep fakes are a reasonably new phenomenon. It is not a social engineering tool in itself but can be used as part of an attacker's toolkit. Machine learning is used to create multimedia content, such as images, audio and videos that can mimic a real-life person. There are not many examples of this technique being used at scale however, even if a few examples exist – it is still cheaper and easier to send out phishing emails.
Conclusion
I could end this selective summary with a very long bullet-list of social engineering 'red flags’; however, to do so would risk falsely ‘immortalising’ methods that are in fact continually evolving, and often change during the interaction between a perpetrator and a victim. There are several well-functioning technical protection mechanisms that aid in stopping cyber-related social engineering attacks, but the weakest link in the chain is still the human being. Attacks that slip through the net, and physical attacks, require vigilance and education. The right mindset will help you to stay on your toes. It is perfectly fine to be suspicious without being paranoid – I call it a healthy distrust. It will help you a long way in developing good security hygiene… Finally, don’t click on links or open attachments from sources you don’t know or trust.
